RKE2: A Simple to Deploy Secure and Compliant Kubernetes Distribution for Demanding Environments
In the ever-evolving world of container orchestration, Rancher Kubernetes Engine 2 (RKE2) stands out as a powerful and secure solution. This next-generation Kubernetes distribution from Rancher Labs caters specifically to the needs of organizations, particularly those in the U.S. federal government sector, that require robust security and strict compliance adherence.
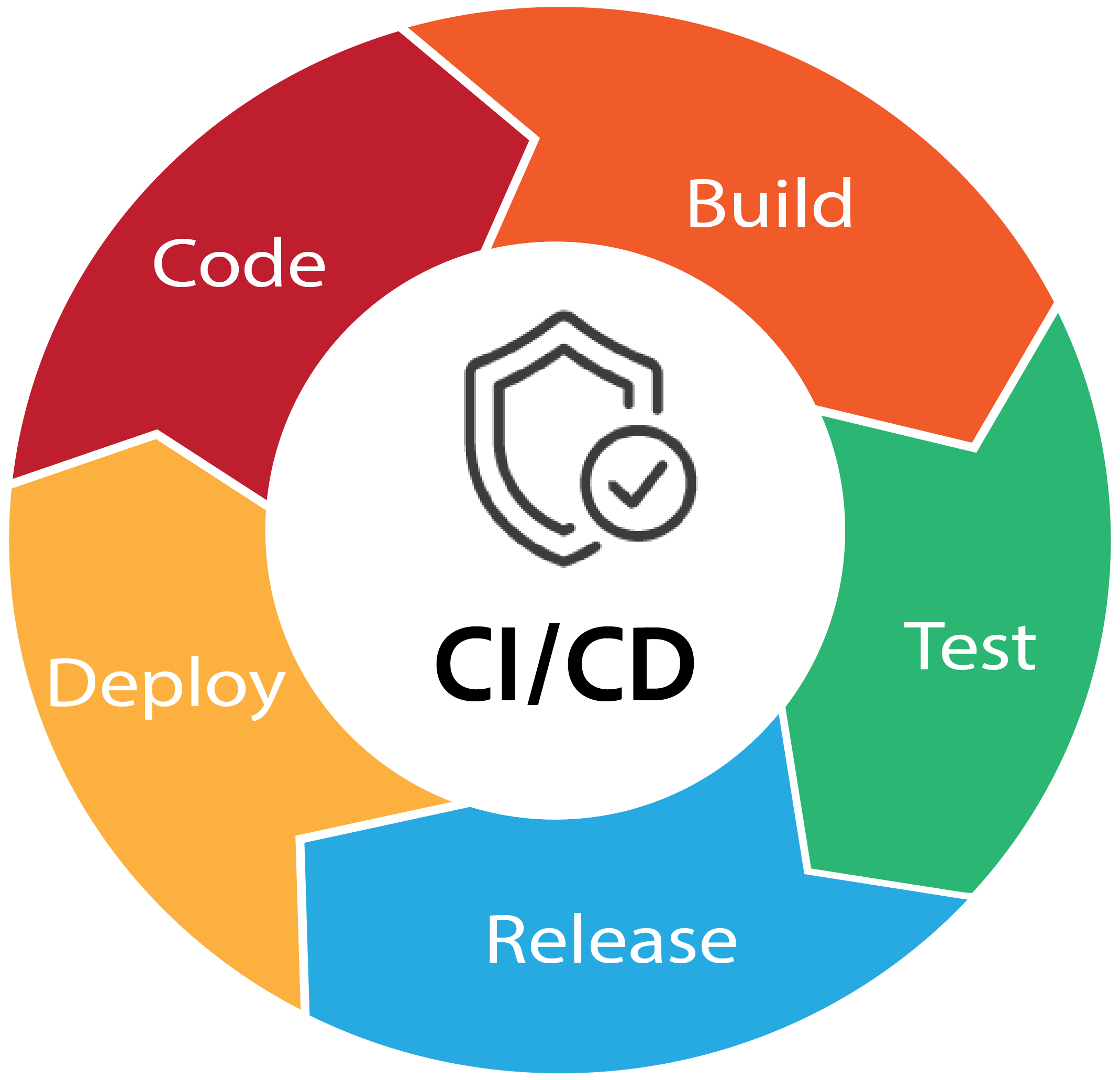
Building a Secure CI/CD Pipeline: A Guide to Safer Software Delivery
In today's fast-paced software development landscape, Continuous Integration and Continuous Delivery (CI/CD) pipelines are the backbone of efficient delivery. However, security must be a top priority, as a compromised pipeline can expose your code, customers, and reputation to significant risk.
Secure Your Business: Top 5 Actions Every SMB Should Take
In this article we tackle pressing concerns for small and medium-sized businesses (SMBs). Today, we're diving into cybersecurity, a crucial aspect of protecting your valuable data and operations. We'll cover the top 5 actions you can take to secure your infrastructure, along with recommended products and services to get you started.
Decoding Gen AI: Hype, Hope, and How Businesses Use It Now
Remember playing with Play-Doh as a kid, squishing and shaping it into fantastical creatures? Well, imagine AI with similar superpowers, churning out new content like text, images, and even code – that's what Gen AI does!
Cybercriminals are impersonating you and stealing your customer’s data!
Cybercriminals use email spoofing to trick recipients into thinking that an email is from a legitimate sender. This can be done by forging the sender's email address, display name, or both. In some cases, the spoofed email may even contain logos or other branding from the legitimate sender to make it appear even more authentic.
Phishing: What You Need to Know to Stay Safe
Phishing is a type of social engineering attack that uses fraudulent emails or websites to trick victims into giving up their personal information, such as passwords, credit card numbers, or Social Security numbers. Phishing attacks are one of the most common types of cyberattacks, and they can be very successful.
Why do small business need a help desk?
In today’s fast-paced digital landscape, businesses rely heavily on technology to drive their operations. This is where a dedicated Help Desk comes into play, serving as the cornerstone of an effective IT support strategy. Learn more about this important but often overlooked IT function.